[ad_1]

The latest report by the security-focused ranking platform CertiK revealed two individuals behind a several-million-dollar-heavy scam – and there is a twist to the duo’s partnership.
The report explained that “a number” of scammers had been using a phishing kit known as ‘Monkey Drainer’ over the last couple of months. This type of scam uses the technique called ‘ice phishing’, tricking users into giving the fraudsters full access to their funds.
Now, says CertiK, thanks to a November 2022 incident, two wallets used by two scammers in this type of fraud have been discovered – and this revealed two names: Zentoh and Kai.
The platform stated that,
“Our investigation has determined with a high degree of confidence Zentoh and Kai were behind a fake Porsche NFT website. This site, which utilized the Monkey Drainer tool, was active for approximately two weeks through mid to late November 2022.”
The site can still be viewed via web.archive. It claimed that “for the first time in history, Porsche is offering an original collection of freehand sketches in NFT form in a public free mint available from 11.11.22.”
Can’t trust your partner in crime
During the period of time when the site was promoted online, particularly on Twitter by users and bots alike, people started raising the alarm that the project could be a scam, with one user reporting that the website asked for permission to spend their wrapped bitcoin (WBTC), the report stated. Even though the request was denied, the users allegedly still fell victim to it.
Per CertiK,
“One victim of this particular scam wallet lost $4.3 million in a single transaction. This is one of the most devastating losses to an ice phishing exploit.”
The funds were quickly transferred to another wallet, swapped for the DAI stablecoin, then transferred again.
The victim tried to reach the attacker and ask for the money back, but got only an unhelpful reply in Russian in return. However, another on-chain message, this time in English, was sent to the scammer: to Kai from Zentoh. And it suggested trouble in paradise. Kai apparently betrayed Zentoh, moving the funds from “our wallet” to another one that Zentoh had no control over.
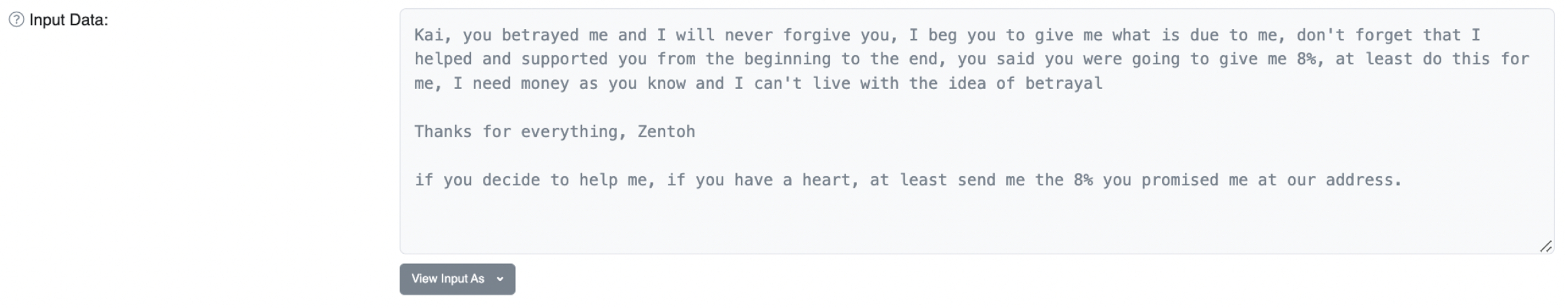
Closing in on Zentoh and Kai
Another on-chain message suggested that the initial conversation about the scam and coordination were done on Telegram.
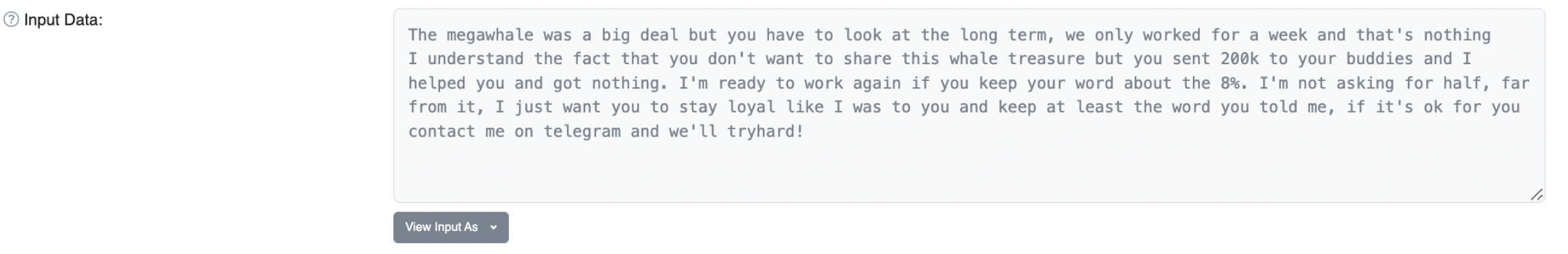
When CertiK searched for ‘Zentoh’ on Telegram, they found an exact match – an account that “has been identified to be running a Telegram group that sells phishing kits to scammers.” The person self-identified as “CEO” at NFT/Crypto drainer channel. The channel even had a tutorial on how the wallet drainers work.
Notably,
“When we analyze the wallet provided in the demonstration video, we discover a clear connection between it and the wallet used by Zentoh to communicate with Kai.”
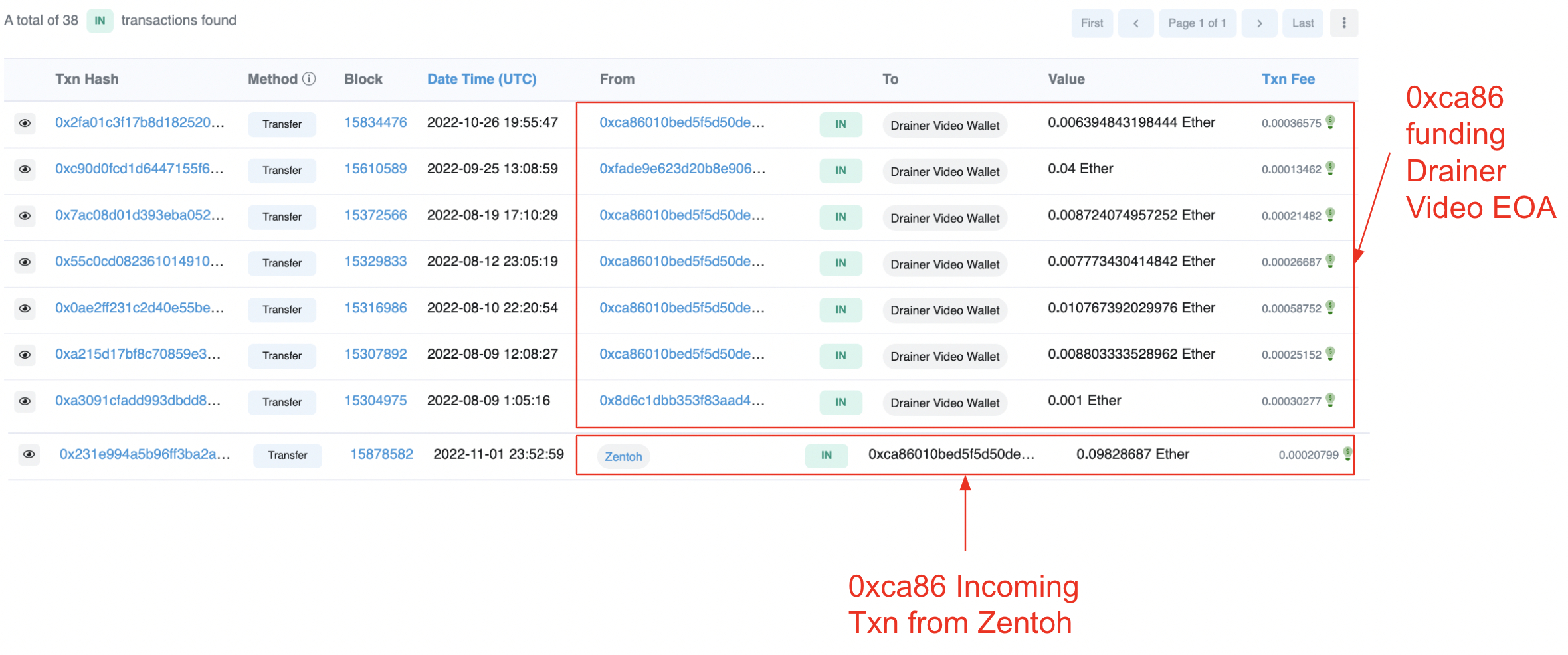
And that’s not all. Per CertiK,
“The two scammers have a direct link to some of the largest Monkey Drainer scam wallets.”
Zentoh, is that you?
Another name is then added to this list: TecOnSellix. This is a Telegram user whom security researcher PhantomXSec had identified on Twitter as a seller of the Monkey Drainer phishing kit. TecOnSellix is also listed as a contact on the above-mentioned NFT/Crypto Drainers Telegram group.
Per CertiK,
“TecOnSellix and Zentoh may be the same person, and 0x32Moon could potentially be added to that list. TecOnSellix is listed as the owner of the Telegram channel Crypto Drainers, which Zentoh’s profile said they were the CEO of.”
The report went on to say that among accounts on GitHub with the name ‘TecOnSellix’, Berrich36 stands out. It said that,
“We have identified a number of accounts attributed to GitHub user “Berrich36”. If the links between these accounts are legitimate and not misdirection, we believe we can link to the real world identity of Berrich36, who appears to be a French national residing in Russia.”
CertiK concluded that Kai was relatively new to the scam at the time of the $4.3 million theft, and that Zentoh is a “key member” in the distribution of wallet drainer tools that make it simple and easy for malicious actors to steal assets from the Web3 community.
Cryptonews.com attempted to contact Berrich36 for comment. If this person would like to respond to accusations, we’d like to hear from them as well.
____
Learn more:
– S Korean Police Probe Possible $8m Crypto Scam Targeting Investors Who’d Suffered Losses
– Canadian Resident Heartbroken After Falling Victim to Crypto Scam, Loses Home and Almost $500K – Here’s What Happened
– Robinhood’s Verified Twitter Account was Hacked and Started Promoting a Crypto Scam – This is What Happened Next
– Missing ‘Cryptoqueen’ Ruja Ignatova’s London Residence Listed For £11 Million – Where is She?
– Logan Paul Drops Threat of Lawsuit Against Coffeezilla But Will Alleged Victims Get Money Back?
– Eurojust Stops Major Crypto Fraud Network
[ad_2]
cryptonews.com




